While Access Denied in AWS S3 are intended to protect data and control access, they can lead to service disruptions, operational delays and even financial losses if not handled properly. So we need solve it urgently, following provides some methods to fix S3 access denied and the causes of the error.

The AWS S3 Access Denied 403 is a message that appears when you attempt to access an Amazon S3 bucket or object, but your request is blocked due to insufficient permissions or misconfiguration. What we need to do is to solve this error, the answer you can find in this article.
In order to fix the access denied in Amazon S3, you need to review and correct permissions related to IAM users, bucket policies, object ACLs, and other S3 security configurations. The following is a step-by-step guide to help you resolve the issue of access being denied.
Ensure the IAM user you are using has the necessary permissions for the S3 bucket. You can verify this by following steps:
Navigate to IAM in the AWS console.
✶Select the User or Role you use to access the S3 storage bucket.
✶Review the attached policies to ensure they include the necessary actions or other required permissions.
You can follow the below command for full bucket access:
Your S3 Bucket may have a restrictive policy that denies access. If necessary, check and modify the S3 bucket policy by following steps:
✺ Go to the S3 console, and select the bucket that is causing the deny access error.
✺ Click the Permissions tab to review the Bucket Policy then to ensure that it allows the required access.
You can follow the below command to allow public read access:
An object’s ACL may also prevent access, even if your storage bucket policy allows access, you can follow the steps below to be able to validate ACLs:
☛ In the S3 Console, go to a specific object.
☛ Click the Permissions tab for the object.
☛ Review the Access Control Lists (ACLs) to ensure that the appropriate user or group has access.
You can set ACL by using AWS CLI to make an object public-read:
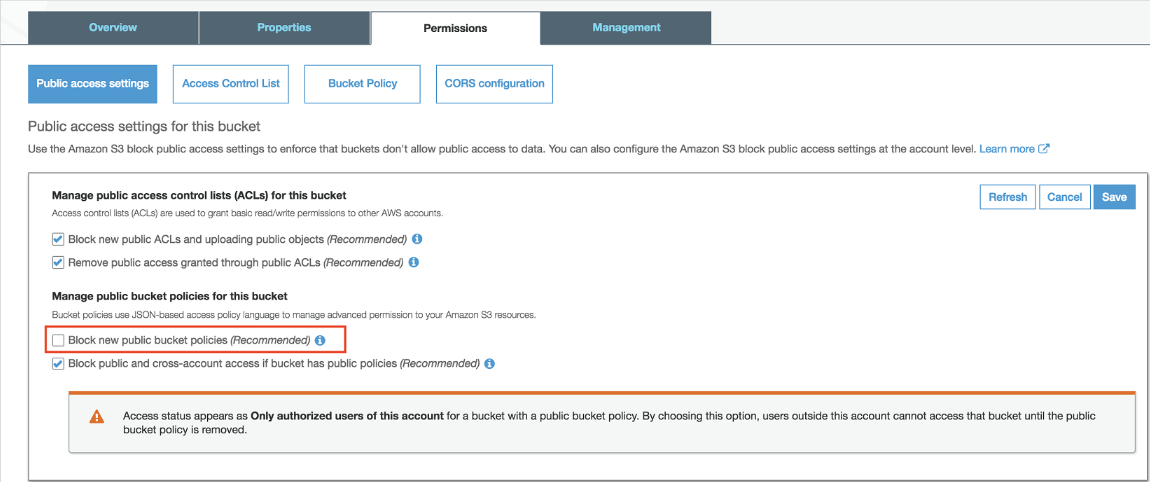
Amazon S3 has a Block Public Access, which can prevent public access to your bucket and objects, even if the bucket policy and ACLs are set up correctly. Follow the below steps to solve this:
❈ Navigate to S3 Console and go to the Permissions tab.
❈ In Block public access to check whether public access is blocked.
❈ If you need to allow public access, modify these settings.
If you’ve already get a s3 Access Denied 403 when trying to access an Amazon S3 bucket, the issue is usually related to permissions. Here are the key reasons for Access Denied AWS S3.
✨Reason 1: Insufficient IAM permissions
Insufficient permissions for the IAM user used to access the S3 bucket. Due to incorrect permissions, your IAM policy may not allow you to attempt to perform a specific action, which could result in access being denied.
✨Reason 2: Incorrect S3 Bucket Policy
The bucket policy defines the operations that are allowed or denied. Access may be denied if the policy has restrictions, such as restrictions based on IP addresses, VPCs, or specific AWS account.
✨Reason 3: Object-Level Access Control Lists (ACLs)
Individual objects in a storage bucket may have restrictive ACLs. Each object in S3 has its own ACL that determines who can access it. An object-level ACL may deny access even if the bucket allows access.
✨Reason 4: S3 Block Public Access Settings
You can enable S3's Block Public Access setting to block access even if the bucket policy and ACL allow access. Amazon S3 has the ability to block public access at the bucket or account level, preventing public access to the bucket regardless of the bucket policy or ACL.
The AWS S3 Access Denied can lead to several drawbacks, especially in environments where reliable access to data is critical. Data security is very important for enterprises, so it is extremely crucial to have a reliable backup software.
AOMEI Cyber Backup is a professional backup software that offers a wide range of backup and recovery solutions, such as system backup, disk backup, partition backup and file backup. The software features a user-friendly design with a simple and intuitive interface that makes the backup process easy to navigate.
Key features of AOMEI Cyber Backup:
✍Automatic Backup: Users can setup an automatic backup schedule. ✍Easy Restoration: Users can simplify the process of restoring data from backups. ✍Fast and Complete Recovery: You have the option to swiftly recover virtual machines from Amazon S3, reducing downtime and minimizing data loss. ✍Multiple Storage Options: You have multiple choice in backup destinations, local disks, external hard drive and cloud service.
1. Navigate to Target Storage and select Amazon S3 > Add Target to open the add target page. Then enter Username, Password and Bucket name, and click Confirm.
2. Go to Backup Task and click + Create New Task to start archiving VMware ESXi backup to Amazon S3. Then select VMware ESXi Backup as Backup Type.
3. Check Archiving backup versions to Amazon S3, and then click Select to choose the added Amazon S3. Backup VMware to AWS helps simplify the backup process and improve data security for hybrid cloud environments.
4. Select Start Backup to begin backup process. It will first create a local or NAS backup and then upload it to Amazon S3.
When you encounter Access Denied 403 in AWS S3, it usually indicates a permission issue related to a data bucket or object. This can be caused by incorrect bucket policies, insufficient IAM user or role permissions, or misconfigured ACLs. Having this error may pose a security risk to your data, so it needs to be resolved in a timely manner and have a professional means of backing up your data to protect it.